Internet Security
5 Shocking Facts About Extortionware You Need to Know
Malware is available in various forms and one of the examples of which is extortionware. Ransomware is something you could
Firefox 124.0
Mozilla has recently released the Firefox 124.0 Stable along with its 115.9 ESR. This new, updated, stable version of Firefox
How to Fix a Google Chrome Not Enough Memory Error
Google Chrome is one of the popular browsers among users. Although it is an excellent browser overall, it also has
Best URL Scanners
If you want to inspect any website for malicious infection to keep yourself safe against viruses and phishing activities, you
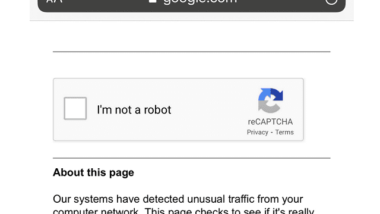
Google’s “Unusual Traffic” Error
An error message is the simplest way to inform users that their device or software is facing a problem. You
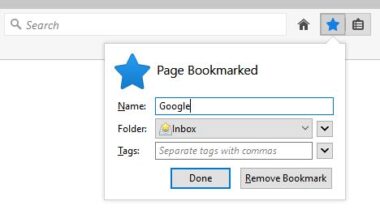
Bookmark Manager
Whether you agree or not, it is true that we get the most information from the internet. For instance, we
SOVA Android Trojan
SOVA Android Trojan is a new type of mobile banking malware campaign that aims to target banking customers. Its first
Pokémon Scarlet and Violet
Generation IX comes with two primary paired versions, including Pokémon Scarlet (Japanese: ポケットモンスター スカーレット Pocket Monsters Scarlet) and Pokémon Violet
What is Bluebugging?
Nowadays, most people have mobiles, and Bluetooth is one of the standard mobile features you can use frequently. But one