Blog
TCP Vs UDP: What’s the Difference?
Do you want to know what is the difference between TCP and UDP? Then, you have come to the right place. In this article, we are going to discuss TCP Vs UDP. If it comes to differentiate these two, you need to know a lot of things. TCP and UDP are known as Transmission Control Protocol and the User Datagram Protocol, respectively
These two are both communication protocols.
A User Datagram Protocoll is usually rapid and updated. However, multiple systems are still using the Transmission Control Protocol for downloading batches of information. So, if you want to make the right decision, then check the specific IP needs. To help you in this case, we cover all the important points about these two. This article discussed their purposes, working process, features, functions, applications, etc. We have also given the difference between these two protocols elaborately.
What is TCP:-
It is known as the Transmission Control Protocol. This protocol is connection-oriented. That means it can transmit data in two ways after establishing the connection. It comes with built-in systems. With the help of this feature, it can check errors. These make the protocol ideal for sharing details such as still images, data files, and web pages. Undoubtedly it is reliable. Along with this protocol, the feedback mechanism allows you to use the Bandwidth wisely on your network.
It comes with a built-in retransmission feature also. You can use this as a telephone connection. When you use a telephone connection, your first job is to fix the connection. To do this, you need to dial the number first. As soon as you receive the answer from the other end, a two-way communications channel is established and made available. After that, you can speak. When you are done with this, it allows you to hang up the connection.
This Transmission Control Protocol transport makes you sure that there presents no error in the received data. It is similar to a telephone connection. Except for you, no one will be unable to use the connection while you are using it. Application protocols that require guaranteed message delivery can use the protocol. HTTP, FTP, SMTP, POP3, IMAP4,.etc; are some examples of Internet application protocols. It helps to establish even reliable connections. This protocol relies on IP.
The Transmission Control Protocol is a part of the transport layer of the ISO’s open system interconnection (OSI) model. It implies that the protocol is a transport layer communication protocol. There is also a method to know whether you are using this one or not. The buffering symbol will let you know this.
Transmission Control Protocol
When you want to load a high-quality video, you can see this buffering. It allows you to know that the protocol helps to transmit the receiving data. The main objective here is to transmit data without making an error. It makes sure that you have got all the essential information. The delivery report ensures this case.
It organizes the data appropriately and ensures that the recipient receives the packet according to the order. The established connection confirms that the process has been done successfully. Generally, when the sender sends the data, he also gets a confirmation from the recipient. In case it doesn’t happen, the protocol tells the sender to send it again. It was the Internet Engineering Task Force (IETF) that defined the protocol first in RFC 761. After some time, the protocol was obsoleted by RFC 793 in 1981.
It is a very famous transmission data process protocol. However, it is not ideal as you will not be able to use this in all cases. That’s why people use the User Datagram Protocol. Usually, it is the IP protocol that helps to break the information into packets. And after that, it helps to send them to their destination.
The prime purpose of its invention is to put the packets back together after the arrival. As soon as the packets reach their destination, the receiving device helps to resemble them in their original form. You need to take the help of both parties to establish a connection and sending information. For every packet, the recipient sends a confirmation message to the sender. In the header, there exists a checksum. It helps to check the packets and to confirm whether there presents any error or not.
Features of TCP:
Here, we have given some features of the transmission control protocol.
Data delivery:
It makes sure that you have got the complete information correctly and all the data is present. When you don’t use this one, you may receive Incorrect data. For instance, suppose we are trying to see the web page. Or we want to download a file without the help of the protocol. If it happens, we may miss some information or pictures.
Protocol:
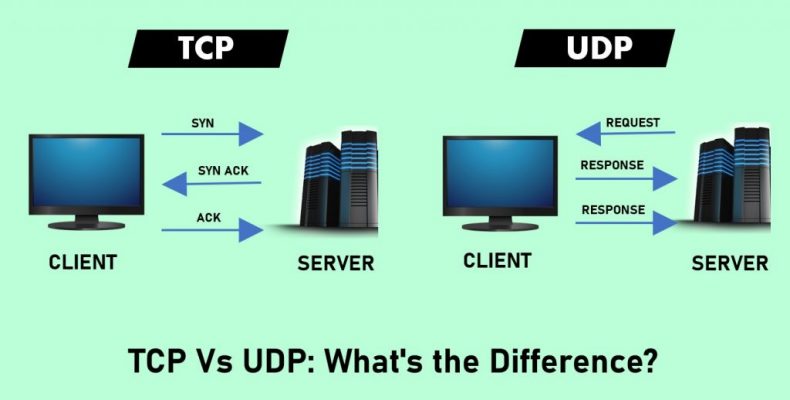
It is this connection-oriented protocol that helps us to understand that computers make a connection first. After that, it does the communication. A three-way handshake is helpful in this case. In this process, an SYn message goes to the receiver from the sender side. Then, the receiver gives an SYN-ACK message. It lets us know that the message has been delivered. As soon as the sender gets the SYN-ACK message, he/she transfers the acknowledgment message. Thus, you can make a connection between computers.
How It Works in Exchanging Data
The three-way handshake process needs a transmission control protocol to send data packets to the client. Here, both sender and receiver exchange the SYN, SYN-ACK, and ACK messages. We know these as flags. These let you know that you have made a reliable connection between them. An example of these three-way handshake messages are as follows:-
SYN — synchronize
SYN-ACK — synchronize-acknowledgment
ACK — acknowledge
There are plenty of other flags also which you can exchange. As soon as you make the connection, the messages will get transferred. There presents an ACK flag whenever data transfer occurs. It confirms the receipt of the data. The internet video streaming service Netflix used the protocol as of June 2016.
Opportunities for Transmission Control Protocol
It is non-proprietary. Besides, the protocol provides a reliable full-duplex connection with Transmission Control Protocol Streams. It also offers a 3-way handshake, credit flow control, fast retransmission and recovery, Selective-ACK, and scaling. The protocol supports all different types of operating systems along with various kinds of computer hardware and networks. It increases the chances to use this internet protocol suite across all the markets.
TCP Functioning:
The functions of this protocol are as follows:-
(i) Addressing and Multiplexing: You need to use the ports to address different methods of the network for upper-layer applications. The protocol helps to multiplex the information which you store using other methods. After that, it helps to broadcast the data packet with the help of the network access layer.
(ii) Set-up Sustain and Terminate Connections: Here, you need to follow every step of the methods and rules for fixing a connection between the source and destination end. You have to follow the handshake protocols & procedures. With the help of these, you can acknowledge the ongoing communication process. At last, you have to follow a few rules for terminating the connection after ending up the communication between the source and destination side.
(iii) Packaging of Data: The protocol packages the data into message format to transfer them. After that, it sends the packets to a higher layer for communication. Next, it will deliver the packet to the destination. Here, the person sitting at the receiver decodes the information and unpack it. Then, it transfers the data to the upper layer applications.
(iv) Reliable Mode of Communication and High QoS: Transmission Control Protocol provides a reliable mode between a sender and receiving end to communicate. You can get a top-quality service also using the protocol. It uses a mechanism to share data that follows a set of rules. In addition, it confirms that you have got the data. Moreover, it uses various types of handshake protocols for ensuring reliable communication.
TCP Applications:
People use this protocol in FTP which stands for File transfer protocol. It helps to transfer big data files within any organization—no matter whether the hosts are far away or not.
When you share emails, it follows the Simple mail transfer protocol (SMTP). This one also takes the assistance of TCP to send large files. You can share them among different hosts both inside and outside of the organization.
POP uses it to recover and download email messages.
The TELNET protocol needs TCP to get access to the host by logging in to them. It allows you to gain access to the host who is far away from you.
The Border gateway protocol (BGP) uses it to provide a reliable mode of communication. It has usage in the military services also. They use it to exchange highly confidential information on their internet.
Advantage
The benefits of Transmission Control Protocol are as follows:
- It can be operated independently of the OS.
- Along with supporting many routing protocols, it allows you to work within networks between the organizations.
- It features a highly scalable client-server architecture. Besides, you can use it independently.
- Moreover, it is compatible with various routing protocols.
- You can use it to establish a connection between two computers.
Disadvantages
The drawbacks of the protocol are as follows:-
- Unless it asked explicitly, the data transmission process would not complete
- It doesn’t allow the user to use it for broadcast or multicast transmission.
- You have to make block boundaries as it doesn’t have any.
- It comes with a lot of unnecessary features, which can waste Bandwidth, time, or effort.
- The transport layer of the model is unable to provide you a guarantee for the delivery of packets.
- You can’t replace it with ease. Along with this, the model does not provide separation from its services, interfaces, and protocols.
What is UDP:
The complete form of it is User Datagram Protocol. It is an easy and connectionless Internet protocol. In this case, you don’t need to check errors and recovery services. There remains no overhead to make a connection using it, maintain the connection, and terminate it. Here, the data transfer process is running continuously to the recipient. It does not matter whether the sender is receiving the information or not. However, it is not the exact one for those who want to send an email, view a webpage, or download a file using it.
Mostly, people use this for real-time communications. For instance, they use the protocol for Broadcast or multitask network transmission. You can use email to send your message. The only problem is that you will be unable to understand whether the other person has got the message or not. It does not help you to correct or recover errors in the message. It is the receiving application that is responsible for this. The reason is that there doesn’t present any connection set-up.
User Datagram Protocol
The speed of the User Datagram Protocol is quicker compared to the transmission control protocol. That’s why it faces less network traffic. Apart from this, there are no resources on the receiving machine. It is because the User Datagram Protocol doesn’t hold a connection open. Examples of applications that use the protocol are DNS, DHCP, RIP, etc. It is used mainly for boosting with IoT. The reason is that the sensor type data is perfect in this case. You should know that both datagram and packet are quite similar. User datagram protocol comes with built-in features of IP protocol. Besides, the working process of this protocol is quite the same as the previous one.
It does not need to transfer an acknowledgment message to the recipient. It is the main difference between TCP vs UDP. In this case, packets that get lost are never resent. With the help of this one, computers can make communication even faster. However, the sent data may not match with the received data. The packets don’t come with any sequence number. It comes with checksums that help the packets to protect them against corruption or modification.
Features of UDP:
Here, we have given a few features of the User Datagram Protocol. Let’s have a look.
- This transaction-oriented model is ideal for simple query-response protocols. Domain Name System or the Network Time Protocol are examples of these.
- Datagrams provided by User Datagram Protocol are perfect for modeling other protocols. For example, it is ideal for IP tunneling, remote procedure call, and the Network File System.
- You can use this for bootstrapping or any other cases. It does not even require a complete protocol stack. DHCP and Trivial File Transfer Protocol are a few instances of it.
- This protocol is ideal for multiple numbers of clients like streaming media applications— IPTV.
- It reduces delaying of retransmitting data. This feature makes it perfect for real-time applications. You can use this for Voice over IP, online games, and other different cases.
- The protocol is compatible with multicast. Besides, you can use this to broadcast data in different cases. It helps to broadcast data like Precision Time Protocol and Routing Information Protocol.
How it Works in Exchanging Data:
The primary advantage of this one is that it provides lower latency. However, during this period, some data, as well as data integrity, is also lost. In case the data is not found, the sender is not going to send it again. It is because there doesn’t exist any process to confirm that the receipt gets the message. You can use this to transfer information quickly. During this time, the data do not remain the same as it was. There is a chance of data missing.
People need to use this for “live” situations as it is perfect for it. For example, you can use this where data transfer can occur without any delay. Online video gameplay and audio or video calls are some examples of it.
UDP Functioning:
(i) Higher-Layer Data Transfer: It receives the data from the higher layer first. Then, it helps to convert it to the UDP messages. After that, it sends the information to the User Datagram Protocol software to start communication.
(ii) Message Encapsulation: The header part combines the source port and destination port domains. It helps to know the value of the checksum also.
(iii) Message Transferred to the Next Layer: When the above procedure is completed, the message then goes to IP for communication. After that, the method gets reverted when it is at the destination end.
Applications:
If you want to stream videos, audio you need quick data speed. In this case, it doesn’t matter whether the lost data is recovered or not.
You can use this to play video and graphic games online. Users can use it for tunneling processes and VPN networks where they can recover the lost data.
You can use it for broadcasting purposes also for the LAN network.
The widespread usage of this protocol is to watch TV on mobile phones in real-time.
Opportunities for UDP
It decreases the need for computer resources. Since it needs a limited resource, multicast or Broadcast of real-time packet transmission is possible. It can generate demand for small-scale networks over high transmission speed.
Advantage
The prime advantages of the protocol are as follows:-
You can use a connection-based communication model using it at any time. Due to this, startup latency is low in distributed applications.
It comes with Broadcast and multicast transmission features.
In addition, it allows the user to use it in small transactions.
Besides, it comes with a Bandwidth intensive app that endures packet loss.
Disadvantages
Here, we have given a few disadvantages of this protocol. Let’s have a look at this.
Users are not able to resend the packets again.
It is not so compatible with routers also. As a result, retransmission never happens when it collides.
It features no Congestion Control and flows control. Therefore, the primary task of any user application is implementation.
TCP Vs UDP Differences
To know about these two in detail, check the difference between TCP and UDP. We have given almost all essential points of the two transport layer protocols. The primary purpose of this short introduction is to let you know about the difference shortly. It allows you to know why these two transport layer protocols are essential, why both use IP protocol, etc. Usually, the primary purpose of designing applications is to use one or another protocol based on their needs. These two are the most common protocols which people like to use to send packets.
Let’s have a look at the key differences between these two.
UDP vs TCP:
Connection Vs Connectionless (TCP Vs UDP)
We know Transmission control Protocol as a connection-oriented protocol. It helps to make connections between both sender and receiver. On the other hand, the User Datagram Protocol is connectionless. It does not make any connection before sending information.
Reliability
People prefer to use Transmission Control Protocol for its reliability. When you transfer information using this, you can ensure that the data is delivered to the receiver. In case you lost the information by mistake, it helps to get the data again. Then, you can resend it. With the help of this, you can track packets along with checking errors. It confirms that no data is corrupted.
The User Datagram Protocol is not so reliable. Therefore, you don’t get any guarantee while delivering data. In this case, you may face a corrupted datagram packet.
Game Servers
When it comes to multiplayer online (MMO) games, it becomes hard for the developers to choose any one of these. The benefits of transmission control protocol are persistent connections, reliability, etc. Besides, it can use packets of arbitrary sizes also. However, there is a drawback with the protocol. It is the congestion control algorithm that marks packet loss as a sign of bandwidth limitations. If you are using 3G or Wi-Fi networks, then you can face a significant latency. You can use HTTP for occasional, client-initiated stateless queries replacing this protocol. Besides, you need to take the help of persistent plain TCP sockets while both client and server send packets independently. In this case, occasional delays can occur. You can use Online Poker, different MMOs, and many more.
However, you need to use User Datagram Protocol when the occasional delay is not ok. You need to use them for multiplayer action games, some MMOs, etc.
Flow Control
Transmission Control Protocol takes the help of a flow control mechanism. It makes sure that the sender is not transferring too many packets at a time to the receiver. This protocol collects information in a send buffer. It uses a receive buffer to receive data. As soon as the application is ready, the protocol can read the information from the receive buffer. Sometimes, the received data becomes full.
As a result, the receiver is unable to handle more information. It causes the loss of data. The receiver says about the room space available in the receive buffer to the sender. The main purpose of this is to maintain the amount of transferred data. Each time there exists a message after the delivery of the packet of data.
On the flip side, the User Datagram Protocol does not come with any flow control feature. In this case, the packets will arrive continuously, or these will get dropped.
Ordering
TCP transmissions are sent and received in the same sequence. If the data segments are not ordered correctly, it helps to rearrange them in the proper order. After rearranging them, it helps to deliver the data to the receiver.
The message sequence is not maintained in the proper order for user datagram protocol while reaching the receiving application.
Speed
Compared to the User Datagram Protocol, the transmission control protocol is a lot slower. People use the protocol to set up connections, error-check, etc. It confirms that the receiver will get all the files in a proper order quickly.
Method of Transfer
In Transmission Control Protocol, data is read as a byte stream. It transmits messages to segment boundaries.
On the other hand, for User Datagram Protocol, UDP messages can be sent individually. In this case, packets define boundaries.
Error Detection
For Transmission Control Protocol, you get both error detection and error recovery features. It comes with a checksum that helps to detect errors. The receiver doesn’t acknowledge a packet whether it is erroneous. If it happens, the sender needs to retransmit the data. This mechanism is known as PAR. It stands for Positive Acknowledgement with Retransmission.
On the flip side, the working process of the other one is on a “best-effort” basis. It is compatible with error detection with the help of a checksum. As soon as it detects an error, it discards the packet. It doesn’t try to retransmit the packet for recovery. People use this protocol especially for time-sensitive applications such as gaming, voice transmission, etc.Usage
The Transmission Control Protocol is suitable especially for those applications that need high reliability. In these cases, timing should not be a matter of tension. Wide Web (HTTP, HTTPS), Secure Shell (SSH), File Transfer Protocol (FTP), and Email (SMTP, IMAP/POP) are examples of these.
A User Datagram Protocol is perfect for those applications which need both speed and efficiency. You can use this for VPN tunneling, Streaming videos, Online games, Live broadcasts, Domain Name System (DNS), Voice over Internet Protocol (VoIP), Trivial File Transfer Protocol (TFTP), etc.
Headers
The header size of the User Datagram Protocol is 8 bytes, whereas the other one is 20 bytes. In both cases, you can get 16-bit source and Destination Port fields. You can use the source port field for sending replies to the message.
Ports
Each of the transport layer protocols uses ports. If you want, you can keep an app on your computer with the help of Transmission Control Protocol port 80. You can use the User Datagram Protocol port 80 also to keep another application. The address of an application may look like ” IP address + protocol (TCP or UDP) + port number.”
TCP Header Format:
Every header comes with ten required fields. The total size of the fields is 20 bytes (160 bits). It includes extra data, which is up to 40 bytes in length. Usually, the header starts with a source and the destination communication endpoints.
Source Port Number (2 bytes or 16 bits):
It refers to the sending device.
Destination Port Number (2 bytes or 16 bits):
It implies the communication terminal for the receiving node.
Sequence Number (4 bytes or 32 bits):
DATA sending node uses these for marking the order of a group of message packets.
Acknowledgment Number (4 bytes or 32 bits):
All senders and receivers use it. With the help of this, users can communicate the sequence numbers of sent or received messages.
Data Offset (4 bits):
it helps store the entire size of a TCP header in multiples of four bytes. Headers that don’t use the optional field of the protocol come with a data offset of 5. It implements 20 bytes. On the other hand, the headers which use the maximum-sized optional field contain a data offset of 15. It represents 60 bytes.
Reserved Data (3 bits):
These have a value of zero. In this case, the total header size is available as a multiple of four bytes. It is essential for the efficiency of computer data processing.
Control Flags (up to 9 bits):
The protocol takes the help of a set of six standards and three extended control flags. Every flag helps to manage data flow in specific situations.
Window Size (2 bytes or 16 bits):
Senders of the protocol use a number which is known as the window size. It helps to regulate the amount of data they send to the receiver. Sometimes, the size of the window is minimal. In case it occurs, you face the network data transfer unnecessarily slow. If the size of the window is very large, the network link can be saturated. Due to this, users can face slow performance. You can use the Windowing algorithms. These help to calculate the size values. Besides, for coordinating changes between senders and receivers, you can use the headers.
Checksum (2 bytes or 16 bits):
The protocol sender creates the value of the checksum inside the header. It works as a mathematical technique. As a result, it can detect corrupted messages.
Urgent Pointer (2 bytes or 16 bits):
Sometimes, it is set to zero. However, you can use it as a data offset with a control flag. It helps to mark a subset of a message.
Optional data (0 to 40 bytes):
The optional data is compatible with special acknowledgment and window scaling algorithms.
UDP Header Format
The size of UDP headers is small in this case compared to the other one. Usually, the UDP header comes with 8 bytes which are divided into the following four required fields:
Source port number (2 bytes): It implies the sending device.
Destination port number (2 bytes): It represents the communication endpoint for the receiving device.
Length of Data (2 bytes): It refers to each datagram’s entire size, which includes both header and data. The field range of the header is from a minimum of 8 bytes to more than 65,000 bytes.
Checksum (2 bytes): Checksum enables receivers for doing cross-check incoming data like Transmission Control Protocol.
Conclusion:
In this article, we have elaborately discussed TCP Vs UDP. On the one hand, TCP helps to set up connections and provides reliable communication.
In comparison, User Datagram Protocol provides a quick communication process. A User Datagram Protocol is a straightforward and connectionless real-time transport protocol. However, it is not compatible with any acknowledgment procedure of sending and receiving data.
Frequently Asked Questions:
- Does Netflix use TCP or UDP?
All types of video streaming such as Netflix, Hulu, Youtube use Transmission Control Protocol.
If speed is a more critical factor than reliability, you need to use the User Datagram Protocol.
- Which is better: TCP or UDP?
A User Datagram Protocol is easy to use and a very quick as well as an effective one. However, you can’t retransmit lost data packets in this case. It is possible only when you use Transmission Control Protocol.