Blog
Smartphone Botnet Army Keeps Growing Stronger
Smartphone Botnet A New Challenge to the Security of Modern Devices
Chipmakers are always on their toes to get rid of any shortcomings, loopholes or vulnerabilities which can be exploited by the cyber criminals for their own interest. A relatively new security firm has left AMD red faced by revealing a wide range of the security vulnerabilities in its chip line-up. This firm gave just a day or two advance notice to the chipmaker before all the flaws and vulnerabilities to the public and this time it is a botnet.
The turning tides in the world of security and information
In the world of security and information tech firms has started making such decisions which are quite questionable and unprofitable to the end users.
No one is able to make out why YouTube has decided to go with the decision of adding Wikipedia links to the controversial videos present on its vast platform.
After more than a year of unrest US finally decided to come up with sanctions against Russia for launching the IRA troll factory and meddling with the presidential elections and even deploying the NotPetya malware on the global scale.
In separate political news it is worth noting that the Florida legislature has come up with a noble way to bring a heightened transparency to its criminal justice system.
This state has successfully staged the fight against the online porn menace in the past and it is doing similar for other threats which are maintained a stronghold in the last couple of years. A popular voice chat host named Zello has been allowing the ISIS accounts remain active on its platform for a long time without taking any action against him.
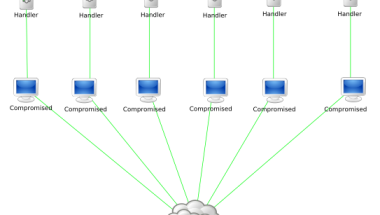
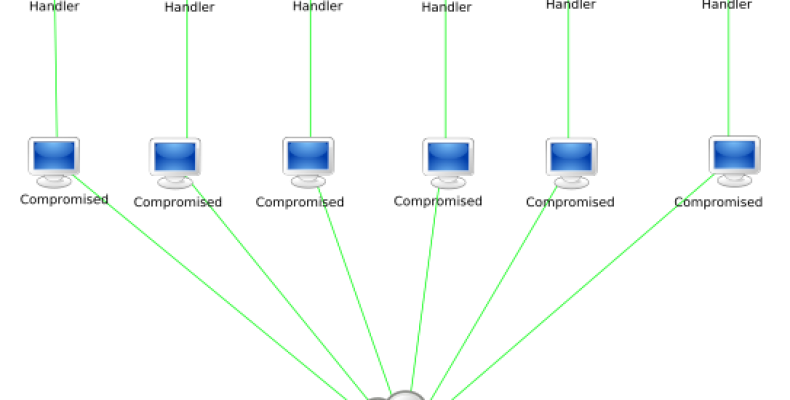
A botnet affecting more than 5 million devices
Security firms have found a new strain of the Chinese malware named RottenSys which had already affected more than 5 million devices.
Smartphone malwares aren’t a new thing anymore as more and more apps are filled with the junk ads. The security firm which uncovered the RottenSys malware maintains this malware exclusively works towards turning the victims into botnet without their knowledge.
At the moment security researchers are unable to understand for what purpose this botnet will be utilized in the future. But it is highly likely that these botnet will be used for a concentrated DDoS attack on massive scale in the upcoming days.
It is worth noting the China doesn’t allow Google Play Store within its territory which means millions of users will not get the benefit of the malware interference offered by it thereby getting more botnets in return.
Through analysing the botnet security analysts has found that attackers are planning to leverage the Tencent’s Tinker application to act as a dropper mechanism.
Utilizing these unusual method attackers will be to launch a large payload by evenly distributing and turning every victim device into a slave of a larger network. The resulting botnet is quite superior when it comes to capabilities and it will have the potential to install additional apps and make use of UI automation upon its will.